
In the ever-evolving world of cryptocurrencies, new threats and vulnerabilities emerge as the technology matures. One such threat that has gained attention in recent years is address poisoning. This subtle yet potentially very harmful attack can cause significant losses if users are not vigilant. In this blog post, we'll explore what address poisoning is, provide some real-world examples, and share practical tips on how you can protect yourself from this form of attack.
What is Address Poisoning?
Address poisoning is a type of attack in the cryptocurrency space where a malicious actor creates and sends a small transaction, using an address that closely resembles one of a user’s commonly used addresses. The goal is to trick the user into mistakenly sending funds to the attacker's address instead of their intended destination.
In many cases, wallet interfaces display only the first and last few characters of an address, making it difficult for users to notice slight differences between addresses. For example, if your regular address starts with "0x1234" and ends with "abcd," an attacker might create an address like "0x1234...abcf" or "0x1234...abdc." If you're not paying close attention, you might inadvertently copy and paste the poisoned address instead of the correct one, leading to the loss of your funds.
This process of creating and sending transactions from spoofed addresses is often automated and used to target users which hold a significant amount of crypto. Address poisoning has led to millions of dollars of crypto being lost over time and continues to be a simple, but effective threat to the crypto industry.
How Does Address Poisoning Work?
The process of address poisoning typically involves the following steps:
Identification: The attacker identifies a target by monitoring the blockchain for addresses involved in recent transactions. These addresses are likely to be used frequently by the owner.
Creation: The attacker then creates a new address that is very similar to the identified address. The similarity might involve changing one or two characters or adding subtle variations that are hard to spot.
Transaction: To get their spoofed address into the target's transaction history, the attacker sends a transaction from this similar-looking address to the target’s address.
Deception: The spoofed address now appears in the target's transaction history or contact list, waiting for the moment when the user needs to make another transaction. If the user mistakenly selects or copies the spoofed address instead of the correct one, the funds will be sent to the attacker.
A example of how a typical address poisoning attack looks in Etherscan is below:
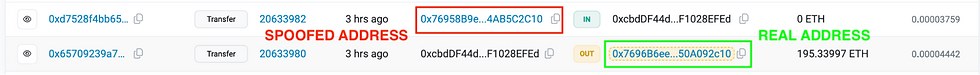
Many crypto wallets and block explorers have noticed these attack transactions and have started to implement features to try and protect their users from attack e.g. by hiding the suspicious wallet addresses from their transaction history. As such, the attack vector has evolved over time to try and bypass these measures and there are now a few different common variants of address poisoning as detailed below.
Small or Low Value Transfers
In order to bypass filtering that has been put in place, sometimes attackers will actually send a small amount of crypto (typically a fraction of a cent) in their poisoning transaction rather than exactly 0. This can sometimes be enough to avoid certain filters put in place to protect users from these attacks.

Zero-Value Token Transfers
Another simple and common variant on address poisoning involves sending zero-value token transfers. Since these transactions involve 0 tokens being transferred, attackers are able to use the “transferFrom” method on ERC-20 token contracts (e.g. USDT) to create a transaction which transfers 0 tokens from an address of their choosing. As such, address poisoning attackers sometimes create zero-value token transfer transactions from the target's wallet to their spoofed address which results in it appearing on block explorers/wallet tracking software as though the target themselves has sent tokens to the spoofed address.

Fake ERC-20 Tokens
Another method involves the creation and distribution of fake ERC-20 tokens. Attackers create a token with a name that closely resembles a legitimate or popular token that the user has interacted with. Transactions involving these fake tokens are then created in the user's wallet and the spoofed address, such that they appear in the user’s transaction history alongside genuine tokens.
When the user sees the fake token in their wallet, they might be tricked into thinking it’s a legitimate token sent from/to a known address. If the user attempts to send further crypto, they might inadvertently select the spoofed address from the transaction history and send their funds to the attackers.

Real-World Examples of Address Poisoning
Biggest address poisoning scam of all time?
There have been several victims of address poisoning scams who have lost significant amounts over time with one large victim losing over $68M in WBTC in May 2024. This victim made a small transfer of 0.05 ETH to an account 0xd9A1b0B1e1aE382DbDc898Ea68012FfcB2853a91 prior to sending the WBTC. The attacker then poisoned the victim’s account by creating a spoofed address, 0xd9A1C3788D81257612E2581A6ea0aDa244853a91, and then sent a 0 ETH transaction from this account to the victim’s account.

The victim then attempted to send 1,155 WBTC to the same address as the 0.05 ETH, but mistakenly sent the WBTC to the spoofed address in this transaction.

This victim lost the WBTC worth over $68M in this transaction from a simple and avoidable mistake. Fortunately in this case, the victim was able to recover the lost tokens however, it should be seen as a lesson to the crypto industry to take care when sending any crypto, especially when sending a large sum.
Pink Drainer falls victim to address poisoning
Even scammers themselves are not safe when it comes to address poisoning - in an incident in July 2024, an account associated with Pink Drainer, the notorious crypto-wallet draining group, fell victim to an address poisoning attack and inadvertently sent funds to a spoofed address rather than their intended destination.
In this attack, the Pink Drainer-associated address sent 10 ETH to an account 0xEfF0E5244d5C78Ba4DD6bc01082576280558f58A. This was immediately followed up by a transaction by an address poisoner transferring 0 ETH from a spoofed address, 0xEfF0eCD2eB275C3CEE4A17D9B8f101551d58f58A, to the Pink Drainer account. Pink Drainer then attempted to send another 10 ETH to the original address, however, accidentally copied the spoofed address and sent 10 ETH to the address poisoner.

This is evidence that address poisoners are indiscriminate and even sophisticated threat actors such as Pink Drainer, who have a lot of experience scamming others, are themselves susceptible to this simple yet effective attack.
How to Protect Yourself from Address Poisoning
While address poisoning can be difficult to detect, there are several steps you can take to protect yourself:

Avoid using transaction history to copy addresses: One of the main tactics used in address poisoning is inserting a poisoned address into your transaction history. To avoid this, never copy and paste addresses directly from your transaction history. Instead, always source the address directly from the service or person you are trying to transact with or a trusted and verified address book.
Manually verify addresses: Always manually verify the full address before initiating any transaction. Rather than relying on the first and last few characters, carefully check the entire address to ensure it matches the intended destination. If your wallet allows, preview the entire address before confirming the transaction.
Utilize an address book: Most wallets offer an address book feature where you can store frequently used addresses. By saving and labeling these addresses, you reduce the risk of copying a wrong or poisoned address. Always use the address book rather than relying on recent transactions or clipboard history.
Employ the spam filtering available on block explorers and wallet software: Many major block explorers and crypto wallets have built in filters to stop spoofed addresses from appearing in your transaction history. When using these services, make sure to double check your settings to ensure you have this filtering enabled to minimize the probability you fall victim to address poisoning. There have been previous reports that the Safe UI did not filter out address poisoning transactions by default on all chains, but zeroShadow worked with Safe to get this feature enabled in July 2024.

Use hardware wallets: Hardware wallets add an extra layer of security by requiring manual confirmation of transactions on the device itself. Since hardware wallets typically display the entire address on their screens, they reduce the risk of address poisoning. This additional step helps ensure that you’re sending funds to the correct address.
Stay educated and vigilant: Keeping up-to-date with the latest scams and security best practices is key to protecting yourself in the crypto space. Understand the nuances of emerging threats like address poisoning and apply the lessons learned to your daily activities.
Conclusion
Address poisoning is a sophisticated attack that targets the common habits of cryptocurrency users, making it crucial to stay informed and vigilant. By understanding how this scam works and adopting robust security practices, you can significantly reduce the risk of falling victim to it. Always double-check addresses, make full use of your wallet's security features, and stay up-to-date with the latest developments in crypto security. Remember, in the ever-evolving world of cryptocurrencies, we are safer together. By working together to share knowledge and best practices, we can protect our assets and navigate the crypto space with greater confidence.
If you have fallen victim to an address poisoning scam, do not hesitate to reach out to zeroShadow for support at help@zeroshadow.io.
Original article by the zeroShadow team

Comments